Google Chrome releases regular updates to bring a ton of nifty features to improve the web-browsing experience. However, sometimes these new updates come with zero-day vulnerability exploits that are a risk to users’ privacy. Thankfully, Google is also quick to fix these vulnerabilities. With its recent Google Chrome 88 update, the company patched a similar zero-day vulnerability that was being exploited by hackers to gain access to users’ system.
The Mountain View-based giant addressed the issue in an official blog post recently. In the post, the company says that Mattias Buelens, a certified security researcher, reported the bug that was in the browser’s WebAssembly and Javascript engine V8. This zero-day vulnerability could lead cyber-attackers to execute code on a victim’s machine and gain access to their sensitive information via Chrome.
There are a few public details about the bug dubbed CVE-2021-21148 as most developers were unaware of the bug’s existence. Google says that it has patched the bug in the latest update. As a result, the company wants its users to update their Google Chrome browser immediately.
“Access to bug details and links may be kept restricted until a majority of users are updated with a fix. We will also retain restrictions if the bug exists in a third party library that other projects similarly depend on, but haven’t yet fixed”, Google wrote in the blog post.
Now, it could be difficult to discover which third-party exploits this bug is related to. However, recent reports have mentioned that the bug might have been used by North Korean hackers targeting security researchers using Chromium-based browsers in a recent cyber attack campaign.
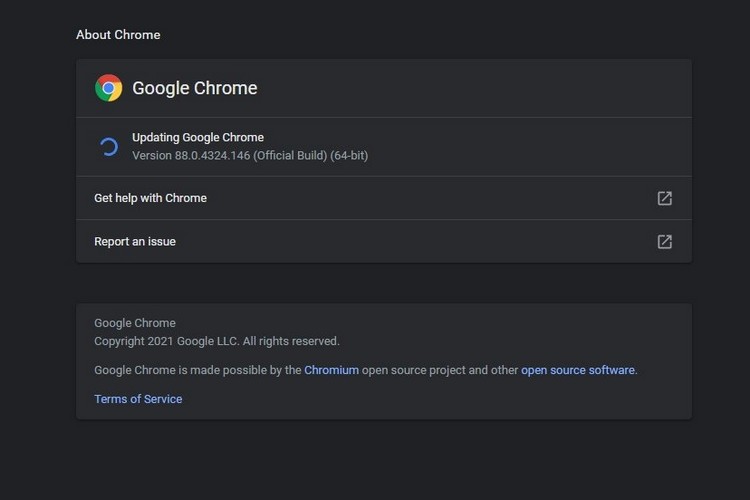
So, to keep your machine safe from these kinds of zero-day exploits, we would recommend you update your browser ASAP. You can do so by opening your browser, going into “Settings”, and opening the “About Chrome” tab from the left tab-bar.










