
- Forensic experts at Beijing Wangshendongjian Forensic Institute have cracked Apple AirDrop to identify the sender and receivers' personal information.
- The experts used the Rainbow Table technique to get information from hashed passwords obtained from iPhone logs.
- China is hailing the new technique as a technological breakthrough.
In a startling new revelation, the Chinese government has claimed to have cracked Apple AirDrop and they can now identify the senders and receivers’ phone numbers and email addresses. AirDrop is Apple’s proprietary file-sharing tool that allows iOS and macOS users to share files with other Apple users. The file-sharing tool is end-to-end encrypted and only shows the device’s name (which can be customized). The new method to bypass the encryption is in direct violation of Apple’s policies.
As reported by Bloomberg, China’s Judicial Bureau shared an online post detailing that The Beijing Institute has devised a technique to extract the records of AirDrop transfers and track senders and receivers’ details. The reason why China has gone after AirDrop is that many people in China use AirDrop to share inappropriate videos and photos on the Beijing Subway and in other public places.
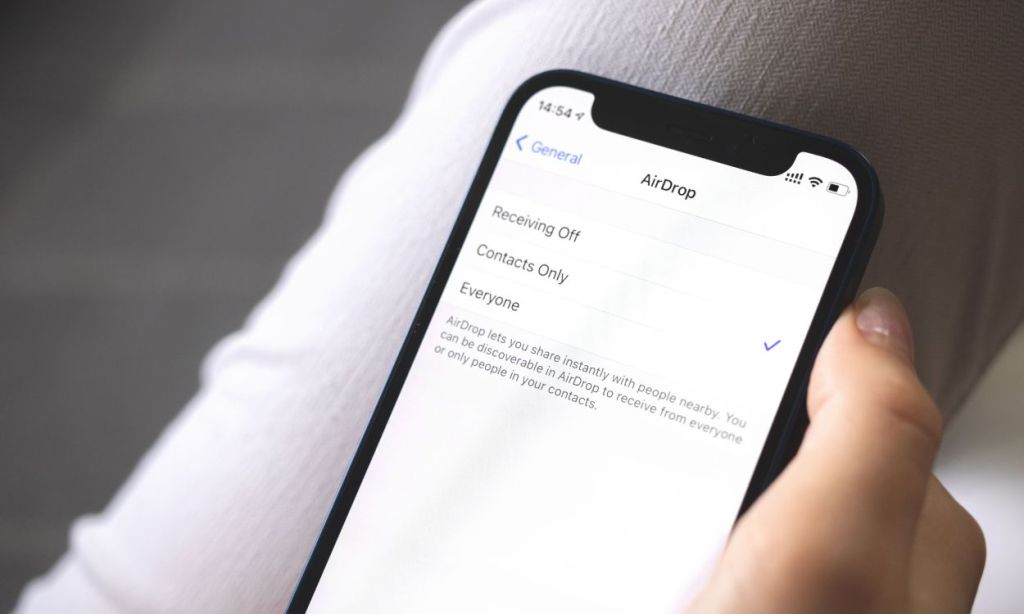
In a recent iOS 17 update, Apple rolled out a feature using which AirDrop can be used to share files without an internet connection. This makes it impossible to track AirDrop contents using contemporary monitoring methods.
In the online post, the Chinese Judia Bureau shared that Forensic technical experts from the Beijing Wangshendongjian Forensic Identification Institute analyzed the iPhone device logs and found that the sender’s device name, email address, and mobile phone number were recorded in the form of hash values. In fact, some of the hashed values were hidden.
To crack AirDrop encryption, the experts created a “rainbow table”. This Rainbow Table consists of mobile phone numbers and email accounts which can convert hashed values into the original text.
For the uninitiated, the Rainbow Table attack is a password-hacking technique that uses a large database of password hash values of commonly used passwords. The hashed passwords from iPhone logs were compared to a precomputed table of hashed passwords. This can help decrypt passwords easily.
Using this technique, police have identified several suspected users who were using AirDrop to share inappropriate videos and photos. The Beijing police have not confirmed whether any arrests were made so far in the AirDrop case.
After receiving several complaints of the misuse of AirDrop in China, Apple added an option to restrict the AirDrop functionality by default to Contacts and added a “Everyone for 10 Minutes” option.
Apple has not issued any statement so far and has not yet acknowledged China’s “technological breakthrough”.










