Announced in March at Google Cloud Next ’17, the Google Titan security chip is another building block in Google’s attempt to punch up its security credentials and narrow the gap with its competitors – primarily AWS and Microsoft Azure. After testing the chip in their data centers for quite a while now, Google recently announced its technical details. So, if you have been coming across news of Google’s Titan security chip and wondering what is it all about. Well, in this article, I will go over what the Google Titan security chip is, how does it work, and everything else that you need to know about it.
What is the Titan Security Chip?
In the simplest of words, Titan is a security chip that prevents the type of attacks where government spies intercept hardware and insert a firmware implant. Currently, the attackers do this mainly by exploring firmware vulnerabilities to overcome operating system defenses and installing rootkits that can persist even after the operating system has been reinstalled.
Titan is a part of Google Cloud Platform (GCP) which is designed, built, and operated with the goal to protect customers’ code and data. The chip is a secure, low-power micro-controller created to ensure that systems always boot from the last known good state. The chip is of the size of a small stud earring and has already been installed in many of the computer servers and network cards that populate Google’s massive data centers.
When the chip was first unveiled back in March of this year, Google planned to use the processor to give each of its servers an individual identity. As of today, Google currently uses the Titan security chips to protect the servers running its own services like Google Search, Gmail, and YouTube.
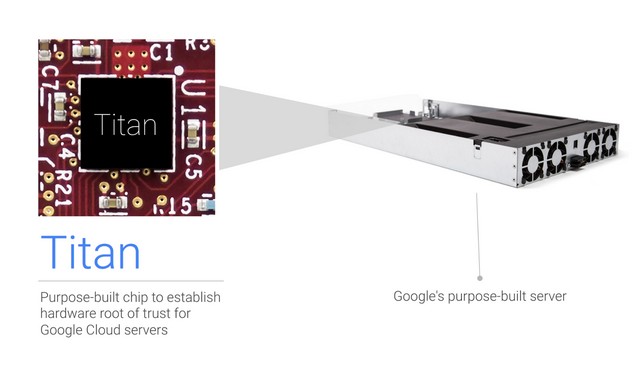
What Does the Titan Security Chip Comprise of?
The machines in Google’s data centers have multiple components including CPUs, RAM, BMC, Network Interface Controller (NIC), boot firmware, boot firmware flash, and persistent storage. These components interact with each other systematically to boot the machines. To protect this boot process, Google uses secure boot which relies on a combination of an authenticated boot firmware and a bootloader, along with digitally signed boot files, to provide the desired security measures.
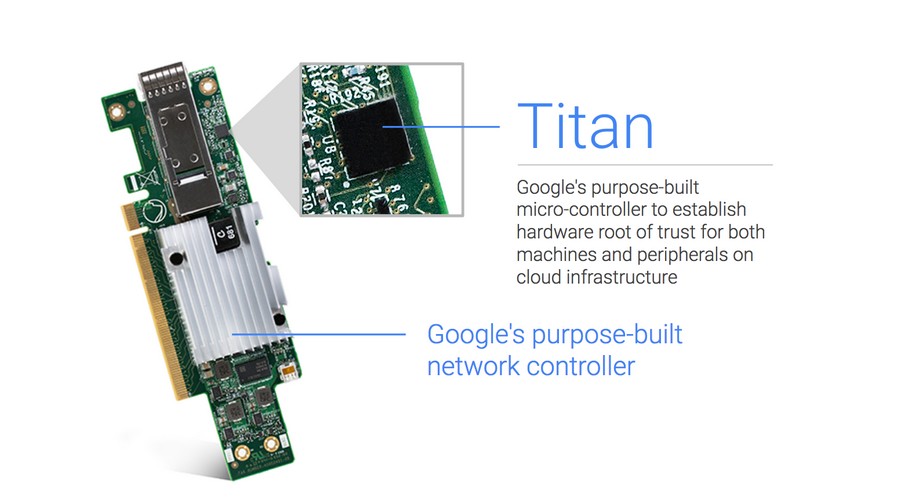
Titan is a specially designed chip that not only meets these expectations but also provides two important additional security properties – remediation and first-instruction integrity. The chip communicates with the main CPU via the SPI bus and interposes between the boot firmware flash of the components like BMC or PCH. This allows it to observe every byte of the boot firmware.
To achieve the security measures that Titan promises, it comprises of several components. Some of the salient ones are mentioned below.
- A secure application processor
- A cryptographic co-processor
- A hardware random number generator
- A sophisticated key hierarchy
- An embedded static RAM (SRAM)
- An embedded flash
- A read-only memory block
- Serial Peripheral Interface (SPI) bus
- Baseboard Management Controller (BMC) or Platform Controller Hub (PHC)
How Does the Titan Security Chip Work?
The first step in the working of the Titan security chip is execution of code by its processors. This is done immediately after the host machine is powered up. Then the fabrication process lays down an immutable code that is trusted implicitly and is validated at every chip reset. Afterward, the chip runs a self test that is built into its memory. This happens every time it boots to ensure that all the memory, including ROM, has not been tampered with.
The next step is to load Titan’s firmware. Even though this firmware is embedded in the on-chip flash memory, the Titan boot ROM does not trust it blindly. Instead, it verifies Titan’s firmware using public key cryptography and mixes the identity of this verified code into Titan’s key hierarchy. Finally, the boot ROM loads the verified firmware.
Once the Titan chip boots its own firmware securely, the contents of the host’s boot firmware flash are then verified using public key cryptography. While this verification is under process, Titan can gate the access for PCH/BMC to the boot firmware flash. Now when the process finally gets completed, the chip sends a signal to release the rest of the machine from reset. This signal provides Google Cloud Platform with the information about what boot firmware and OS are being booted on their machine from the very first instruction. Google Cloud Platform also learns about the microcode patches that may have been fetched before the boot firmware’s first instruction.
Finally, the Google-verified boot firmware configures the machine and loads the bootloader. This subsequently verifies and loads the operating system.
Why the Need for Titan Security Chip?
As most network hardware and servers were made overseas, data center operators working for Google Cloud Platform were concerned about the possibility of nation-state hackers or cyber criminals compromising these devices before shipping them. Google’s Titan chip addresses these concerns through its continual checks which provide additional security to the cloud computing hardware. This allows the company to maintain a level of understanding in their supply chain that they otherwise wouldn’t have.
Another reason why installing the Titan security chip in computer servers is the countering new firmware attacks which can target re-writable firmware chips. These could either be BIOS chips or hard drive controllers.
How Does the Titan Security Chip Benefit Google?
There are two primary ways in which the Titan security chip benefits Google. First is the security point-of-view and second is the competitive point-of-view.
From the security point-of-view, the Titan chip benefits Google in the following three ways:
- It provides a hardware-based root of trust that establishes a strong identity of a machine. This helps Google make important security decisions and validate the health of the system. As a result, this ensures an irreversible audit trail of any changes made.
- The tamper-evident logging capabilities help identify actions performed by an insider with root access.
- The chip offers integrity verification of firmware and software components.

From the competitive perspective, Google Cloud Platform currently has a 7% global cloud market share. This makes it stand third to the likes of Amazon Web Services (AWS) (41% market share) and Microsoft Azure (13% market share). With the new Titan chip, Google is looking to set itself apart from its competitors and bring more security-focused companies to its cloud computing platform. This is an important move as, according to Gartner, the worldwide cloud computing market is worth nearly $50 billion.
As a consequent benefit, Google has also developed an end-to-end cryptographic identity system based on Titan. This can further act as the root of trust for varied cryptographic operations in their data centers.
SEE ALSO: What is Bluetooth Mesh Networking and How It Works?
Will the Titan Security Chip Really Help Google?
While Google Cloud Platform currently falls behind its competitors, especially AWS, the Titan security chip does sound like a great deal for them. With its impressive test results, it all comes down to whether or not the chip will help Google Cloud Services stand out from the others in the longer run. Personally, I am very interested too see how things will turn out. What about you? Do let me know your thoughts on this in the comments section below.


















@Alan Wilcox
I would have to agree with you. Even beyond that there is always a crack in the armor, even if Google completely manufactured the chip in its own USA base facilities.. I think its a endless cat and mouse game and a unwinnable one at that when it comes to digital security.. the only way to have digital information secure is to not have it internet connected and have physical security protecting and controlling access to data (like armed guards) . They may be able to throw hackers of the trail for a moment, but that is all… just for a moment.. they will ALWAYS find a way in if they want one.
There is a $1.5 mil bounty offered by Google to defeat Titan M. While I agree in concept that where it is manufactured and installed could an issue the problem is with human character and integrity not location. NSA and US Government spies on its own citizens so to place blame he usual foreign usual suspects is the normal thought they might start with US intelligence first. If now or in future to If there is a flaw in Titan M someone stands to gain 1.5 mil (USD)
Since this titan chip is most likely made overseas as well, how can google trust it to not have been compromised by some nation state before being installed? If you give the design to another country then you give another country time and the design spec’s they need to compromise anything.
I am wondering here how they plan to mitigate this issue?