Cyber-crimes have been on the rise of late, with ransomware attacks (WannaCry, NotPetya), hacked databases (Equifax, Sony, Yahoo), and software backdoors (Floxif/CCleaner, ShadowPad/NetSarang) making headlines frequently. While the scale and reach of these attacks are astonishing, the fact is, cyber-criminals are not restricted only to stealing your data, identity, or money. The scope of crimes in the virtual world is as large as it is in the real world, if not more. One type of cyber-attack that has been in the focus of late is DDoS, or distributed denial-of-service that have often divided the white-hat hacker community over the years. With leading CDN service provider Cloudflare now announcing free DDoS protection for all its clients, the age-old debate of ‘ethical’ DDoS vs malicious DDoS has started once again, with both sides coming out in full support of their respective arguments. With the debate about DDoS attacks raging all over the internet, let’s take a detailed look at the phenomenon today in an attempt to not only learn more about it, but also to try and understand why hacktivists and free-speech advocacy groups continue to fail in their efforts to come to a consensus about it in the first place:
What is DDoS and How Does it Work?
In the simplest of terms, a distributed denial-of-service (DDoS) attack is an attempt to artificially disrupt normal functioning of a site or network by flooding the target server with an overwhelming amount of traffic that either slows down or crashes the network completely. This is achieved by using multiple compromised systems as part of what’s known as a ‘botnet’ that may include any net-connected device, including, but not limited to, computers, smartphones, and IoT devices. Black-hat hackers as well as hacktivists use various sophisticated tools to carry out these attacks by not only flooding the target servers with an inordinate amount of traffic, but also by using more subtle and difficult-to-detect infiltration techniques that target critical network security infrastructure, such as firewalls and IDS/IPS (Intrusion Detection/Prevention System).

What is DoS and How Does it Differ From DDoS?
Denial-of-service (DoS) attacks is exactly what it sounds like, insofar as it prevents legitimate users from accessing targeted servers, systems or other network resources. As is the case with DDoS attacks, a person or persons carrying out such an attack would typically flood the targeted infrastructure with an inordinately high volume of superfluous requests in order to overwhelm its resources, thereby making it difficult or even impossible for the affected network or system to respond to genuine requests for service. To an end user, the effects of DoS are not entirely different from those of DDoS, but unlike the former that typically uses a single machine and a singular internet connection to carry out the attack, the latter uses multiple compromised devices to flood the intended target, making it incredibly difficult to detect and prevent.
What are the Different Types of DDoS Attacks?
As mentioned earlier, both cyber-criminals and hacktivists make use of myriad attack vectors to carry out their DDoS attacks, but a huge majority of these attacks will, for the most part, fall under three broad categories: Volumetric or Bandwidth Attacks, Protocol Attacks or State-Exhaustion Attacks, and Application-layer Attacks or Layer 7 Attacks. All of these attacks target various components of a network connection that’s composed of 7 different layers, as seen in the image below:
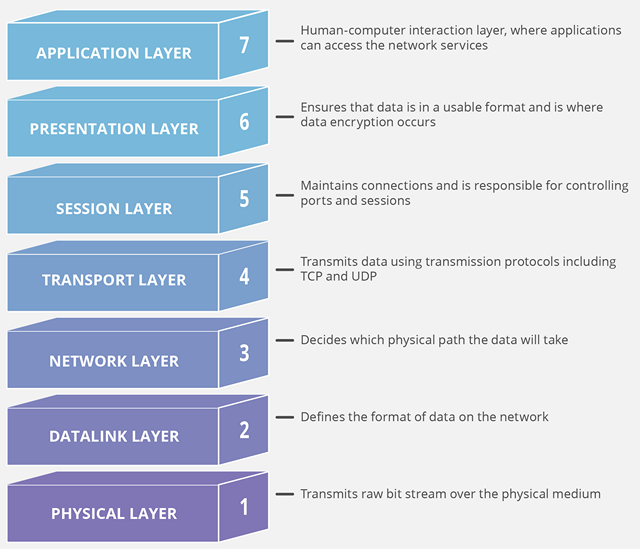
1. Volumetric Attacks or Bandwidth Attacks
These types of attacks are believed to constitute over half of all DDoS attacks carried out around the world every year. There are different types of volumetric attacks, with the most common being User Datagram Protocol (UDP) flood, whereby an attacker sends a large number of UDP packets to random ports on a remote host, causing the server to repeatedly check for and respond to non-existent applications, thereby making it unresponsive to legitimate traffic. Similar results can also be achieved by flooding a victim server with ICMP (Internet Control Message Protocol) echo requests from multiple IP addresses that are often spoofed. The target server tries to respond to each and every one of these bogus requests in good faith, eventually becoming overloaded and incapable of responding to genuine ICMP echo requests. Volumetric attacks are measured in bits per second (Bps).
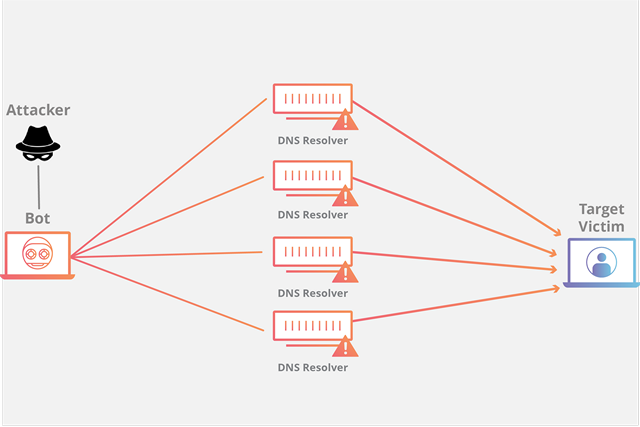
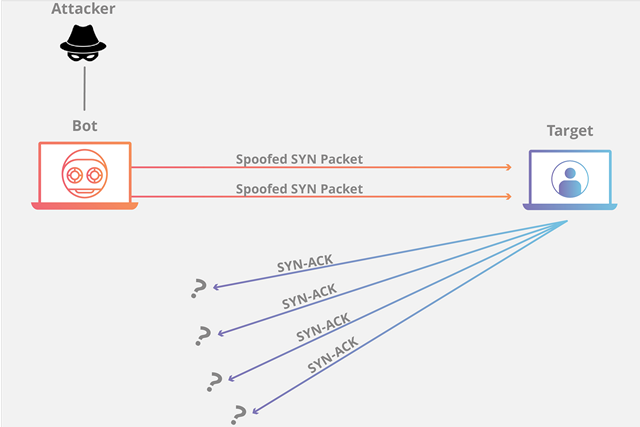
2. Protocol Attacks or State-Exhaustion Attacks
Protocol attacks, also known as State-Exhaustion attacks, consume the connection state table capacity of not only the web application servers, but also other infrastructure components, including intermediate resources, such as load-balancers and firewalls. These types of attacks are named ‘protocol attacks’ because they target weaknesses in layers 3 and 4 of the protocol stack to attain their objective. Even cutting-edge commercial devices specifically designed to maintain state on millions of connections can be badly affected by protocol attacks. One of the best-known protocol attacks is the ‘SYN flood’ that exploits the ‘three-way handshake mechanism’ in TCP. The way it works is, the host sends a flood of TCP/SYN packets, often with a forged sender address, in order to consume enough server resources to make it almost impossible for legitimate requests to get through. Other types of Protocol attacks include Ping of Death, Smurf DDoS and fragmented packet attacks. These types of attacks are measured in packets per second (Pps).
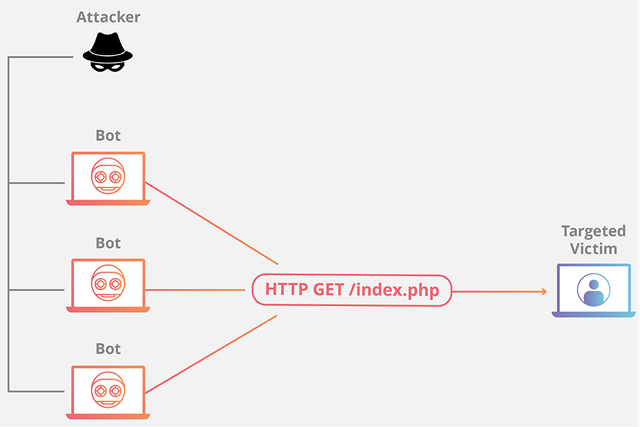
3. Application-layer Attacks or Layer 7 Attacks
Application-layer attacks, often referred to as layer 7 attacks in reference to the 7th layer of the OSI mode, targets the layer where web pages are generated to be delivered to users who are sending the HTTP requests. Different types of layer-7 attacks include the infamous ‘Slowloris‘ attack, whereby the attacker sends a large number of HTTP requests ‘slowly’ to a target server, but without ever completing any of the requests. The attacker will continue to send additional headers at small intervals, thereby forcing the server to keep an open connection for these never-ending HTTP requests, eventually usurping enough resources to make the system unresponsive to valid requests. Another popular layer 7 attack is the HTTP Flood attack, whereby a large number of phony HTTP, GET or POST requests flood the targeted server within a short span of time, resulting in denial-of-service for legit users. Since Application layer attacks typically include sending an unnaturally high amount of requests to a target server, they are measured in requests per second (Rps).
In addition to the single-vector attacks described above, there are also multi-vector attacks that target systems and networks from a number of different directions at once, thereby making it ever more difficult for network engineers to chalk out comprehensive strategies against DDoS attacks. One such example of a multi-vector attack is when an attacker would couple DNS Amplification, which targets layers 3 and 4, with HTTP Flood that targets layer 7.
How to Protect Your Network Against a DDoS Attack
Since most DDoS attacks work by overwhelming a target server or network with traffic, the first thing that needs to be done in order to mitigate DDoS attacks is differentiate between genuine traffic and malicious traffic. However, as you’d expect, things aren’t that easy, given the sheer variety, complexity and sophistication levels of these attacks. That being the case, protecting your network against the latest and most sophisticated DDoS attacks require network engineers to carefully designed strategies so as not to throw the baby out with the bathwater. Because attackers will try their best to make their malicious traffic seem normal, mitigation attempts that involve limiting all traffic will restrict honest traffic, while a more permissive design will allow hackers to circumvent countermeasures more easily. That being the case, one will have to adopt a layered solution in order to achieve the most effective solution.
However, before we get to the technicalities, we need to understand that since most DDoS attacks these days involved chocking off the lanes of communication one way or another, one of the obvious things to do is protect yourself and your network is more redundancy: more bandwidth and more servers spread over multiple datacenters across different geo-locations, which also acts as insurance from natural disasters etc.
Another important thing to do is follow some of the best practices of the industry when it comes to the DNS servers. Getting rid of open resolvers is one of the critical first steps in your defense against DDoS, because what good is a website if no one can resolve your domain name in the first place? That being the case, one needs to look beyond the customary dual-DNS server setup that most domain name registrars provide by default. Many companies, including most of the top CDN service providers, also offer enhanced DNS protection by way of redundant DNS servers that are protected behind the same type of load balancing that your web and other resources are.
While most sites and blogs outsource their hosting to third-parties, some choose to serve their own data and manage their own networks. If you belong to that group, some of the basic but critical industry practices you need to follow involve setting up an effective firewall and blocking ICMP if you don’t need them. Also make sure that all your routers drop junk packets. You should also get in touch with your ISP to check if they can help block wanted traffic for you. The terms and conditions will vary from one ISP to another, so you need to check with their network operating centers to see if they offer any such services for enterprises. In general, the following are some of the steps that CDN providers, ISPs and network admins often employ to mitigate DDoS attacks:
Black Hole Routing
Black Hole Routing, or Blackholing, is one of the most effective ways of mitigating a DDoS attack, but it needs to be implemented only after proper analysis of network traffic and creating strict restriction criterion, as it will otherwise ‘blackhole’, or route all incoming traffic to a null route (blackhole) irrespective of whether its genuine or malicious. It will technically circumvent a DDoS, but the attacker will have accomplished their objective of disrupting network traffic anyways.
Rate Limiting
Another method that’s often used to mitigate DDoS attacks is ‘Rate Limiting’. As it’s name suggests, it involves limiting the number of requests a server will accept within a specified time-frame. It’s useful in stopping web scrapers from stealing content and for mitigating brute force login attempts, but needs to be used in conjunction with other strategies to be able to effectively handle DDoS attacks.
Web Application Firewall (WAF)
While not nearly enough in itself, reverse proxies and WAFs are some of the first steps one needs to take to mitigate a variety of threats, not just DDoS. WAFs help protect the target network from layer 7 attacks by filtering requests based on a series of rules used to identify DDoS tools, but it is also highly effective in protecting servers from SQL injection, cross-site scripting and cross-site forgery requests.
Anycast Network Diffusion
Content Delivery Networks (CDNs) often use Anycast networks as an effective way of mitigating DDoS attacks. The system works by rerouting all traffic destined for an under-attack network to a series of distributed servers in different locations, thereby diffusing the disruptive effect of an attempted DDoS attack.
How Does Cloudflare Propose to End DDoS Attacks for Good with its Free DDoS Protection?
One of the preeminent content delivery networks in the world, Cloudflare, recently announced that it will provide protection from DDoS attacks not only to its paid customers, but also to its free clients, irrespective of the size and scale of the attack. As expected, the announcement, made earlier this week, has created quite a buzz within the industry as well as the global tech media, who are typically used to CDNs, including Cloudflare, either kicking out their under-attack clients or demanding more money from them for continued protection. While victims up until now have had to fend for themselves when under attack, the promise of free, unmetered DDoS protection has been received warmly by blogs and enterprises whose websites and networks remain under constant threat for publishing controversial content.

While Cloudflare’s offer is indeed revolutionary, the one thing that needs to be mentioned is that the offer of free, unmetered protection is only applicable for layer 3 and 4 attacks, while layer 7 attacks are still only available for the paid plans that start at $20 per month.
If Successful, What Will Cloudflare’s Offer Mean for ‘Hacktivism’?
As expected, Cloudflare’s announcement has rekindled the debate among hacktivists and internet security experts about ethical hacking and freedom of speech. Many hacktivist groups, like Chaos Computer Club (CCC) and Anonymous, have long argued that it is necessary to stage ‘digital protests’ against websites and blogs that spread hateful propaganda and bigoted – often violent – ideologies. That being the case, these groups of activist hackers, or hacktivists, have often targeted terrorist websites, neo-nazi blogs and child porn peddlers with DDoS attacks, with the latest casualty being the far-right ‘Daily Stormer’ blog that praised the recent murder of a human rights activist in Charlottesville, Virginia, by a right-wing extremist.
While some, like Cloudflare CEO Mattew Prince, and the EFF (Electronic Frontier Foundation) have criticized hacktivists for trying to silence free speech with DDoS attacks, supporters of hacktivism argue that their digital protests against abominable ideologies are no different than filling a town square or holding a sit-in along the lines of the ‘Occupy’ movement that started with the famous Occupy Wall Street protest on September 17,2011, bringing global attention to growing socio-economic inequality worldwide.
While some may argue that DDoS is a tool for genuine protest, allowing ethical hackers to act swiftly against terrorists, bigots and pedophiles so as to take their immoral (and often illegal) content offline for good, such attacks also have a dark side. Investigative journalists and whistle blowers have often been the targets of such attacks in the past, and it was only last year that the website of cybersecurity journalist, Brian Krebs, was taken down by a massive DDoS attack that measured an insane 665 Gbps at its peak. Krebs had earlier reported on an Israeli DDoS-for-hire service called vDOS, resulting in the arrest of two Israeli nationals, and the attack was believed to be in retribution.
SEE ALSO: 7 Top Cloudflare Alternatives For Your Website
DDoS Attacks and Cloudflare’s Plan to Make Them a Thing of the Past
In spite of Cloudflare’s bold claims of making DDoS attacks a thing if the past, many experts argue that it’s not technologically possible to make DDoS attacks entirely obsolete at this stage. While gigantic corporations like Facebook or Google have the requisite infrastructure redundancies to make sure that they don’t ever suffer from such attacks, extending such protection to every single site under the sun may pose a challenge to even the biggest of CDNs. However, Prince has claimed that Cloudflare is capable of absorbing “anything that the internet throws at us”, so only time will tell if DDoS attacks will be consigned to the annals of history for good, or if hacktivists groups will be able to circumvent some of countermeasures to carry on their moral crusade against violence, hatred and injustice.


















