In April, security researcher Allison Husain discovered a critical security flaw in Gmail’s servers. The vulnerability in question reportedly made it possible for attackers to spoof emails impersonating as any Gmail or G Suite user. As per Husain’s findings, the security flaw even tricks Sender Policy Framework (SPF) and Domain-based Message Authentication, Reporting, and Conformance (DMARC) rules.
Google accepted the issue on April 16 and classified it as priority 2, severity 2 bug. However, the company didn’t immediately follow up on the issue. On August 1, Husain informed plans to disclose the issue within August 17. The software giant acknowledged the issue and set September 17 as the bug fix rollout date. Husain then made the flaw public on August 19. Seven hours later, Google fixed the vulnerability.
As Husain explains in her blog post, the exploit takes advantage of the flawed recipient validation in G Suite’s mail validation rules and an inbound mail gateway to spoof emails. Inbound mail gateway is a server responsible for processing incoming emails.
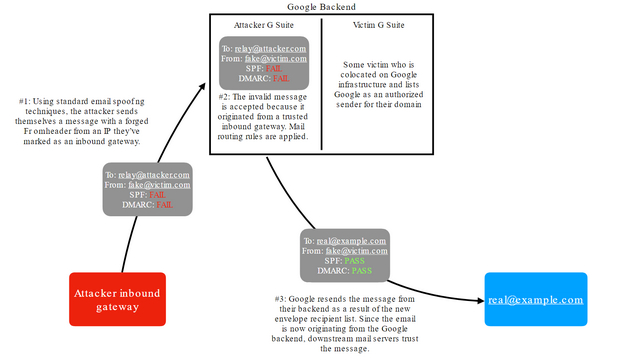
“This is advantageous for an attacker if the victim they intend to impersonate also uses Gmail or G Suite because it means the message sent by Google’s backend will pass both SPF and DMARC as their domain will, by nature of using G Suite, be configured to allow Google’s backend to send mail from their domain,” wrote Husain.
If you’re curious to know how this could have been exploited, Husain has published a proof of concept in her blog post. You don’t have to worry about this issue anymore since Google has done server-side changes to fix the flaw, which means you don’t need to make any changes or update anything on your end.










