The WannaCry ransomware has been in the global spotlight for the past few days after it affected more than 300,000 computers, spread across over 150 countries. It has caused a widespread panic, as no one is sure if they are vulnerable to its attack or not. The Internet is filled with information about WannaCry’s attack, but most of it is incoherent and illegible. It is tough to protect yourself from something you don’t understand. Keeping that in mind we have created a small guide which will help you understand and protect yourself against WannaCry. So, without wasting any more time, let me tell you about the 8 things you should know about WannaCry Ransomware:
What is WannaCry Ransomware?
WannaCry ransomware (also known as WannaCrypt, Wana Decrypt, WCry and WanaCrypt0r), as you can deduce from its name, is a type of ransomware. A ransomware is basically a digital equivalent of a kidnapper. It takes something of value to you and you are asked to pay a ransom amount to get it back. That something of value being your data and files on your computer. In the case of WannaCry, the ransomware encrypts the files on a PC and asks a ransom if the user wants the files decrypted.
A ransomware can be delivered through malicious links or files contained in emails or shoddy websites. WannaCry is the newest addition to a long chain of ransomware which have been used to extort money from people since the 1990s.
WannaCry: How Is It Different From Other Ransomware?
WannaCry, although a type of ransomware, is not your average run of the mill ransomware. There’s a reason behind why it was able to affect such a large number of computers in such a small time frame. Normally, a ransomware requires a user to manually click on a malicious link to install itself. Hence, ransomware originally targeted only a single individual at a time.
However, WannaCry uses an exploit in the “Server Message Block” or SMB to infect the whole network. SMB is a protocol used by a network to share data, files, printers etc. across the users connected to it. Even if a single computer in the network get infected by manually clicking on a malicious link, the WannaCry ransomware will then crawl through the host’s network and infect every other computer connected to that network.
How NSA Helped in Creating The WannaCry Ransomware
NSA (National Security Agency) is known to keep a vault full of exploits which help them to spy on people. Tech giants have been at loggerheads with the NSA to release the exploits, so they can be fixed to prevent cyber attacks, but, to no avail. Once such vault of exploits were obtained and leaked by a cyber criminal group known as the “Shadow Brokers”. The leaked vault contained a tool named “EternalBlue”, which could use the SMB exploit in Microsoft Windows to transfer files without needing user authorization.
Although Microsoft released a patch only a few days after the leak, a vast majority of users did not install the patch before the attack began. WannaCry creators used this exploit in its ransomware to attack computers around the world. Thus, by keeping the exploit active and then losing it to hackers, NSA helped in the creation of WannaCry.
Who Is Behind The WannaCry Ransomware Attack?
Two different technology companies have asserted the similarity between WannaCry ransomware and an earlier ransomware in 2015 developed by hackers who go by the name of “Lazarus Group”. The group is believed to be operating out of North Korea and they are reportedly, they are even supported by the North Korean government. The group is largely known for its attack on the Sony Pictures and Entertainment in the year 2014.
Kaspersky Labs and Matthieu Suiche (cofounder Comae Technologies) have independently written about the similarity of code between WannaCarry and Lazarus’s ransomware. Although it’s still not confirmed, there is a high probability that Lazarus Group and hence, North Korea is behind the attacks.
Systems Vulnerable to WannaCry’s Attack
One of the reasons WannaCry attack has been so successful is because of the fragmented nature of Windows ecosystem. Many networks are still using versions of Windows, especially the likes of Windows XP and Windows Server 2003, which are outdated and no longer supported by Microsoft. Since these older versions are not supported, they do not receive software patches for the exploits discovered and are more susceptible to such attacks.
WannaCry’s attack affected a broad spectrum of Windows systems including Windows XP, Windows Vista, Windows 7, Windows 8.1, Windows RT 8.1, and Windows 10. Basically, If you have not updated and installed the SMB exploit patch on your Windows PC, you are vulnerable to WannaCry’s attack.
How Much Is The Ransom and Should You Pay?
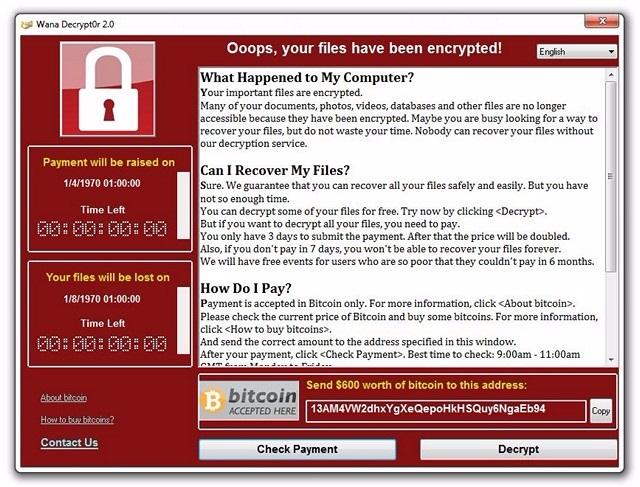
When WannaCry has successfully attacked your system, you will see a window telling you that your system has been encrypted. A link to a BitCoin wallet is at the bottom asking you to pay $300 (US) in the bitcoin currency to get access to your data. If you do not pay within 3 days, the ransom amount is doubled to $600 with a warning that after a week, the data will be deleted forever.
Ethically one should never back-down to the demands of extortionists. But, keeping the ethical point aside, there has been no news of anyone receiving access to their data after paying the ransom. As you are totally dependent on attacker’s whims, there’s no way for you to be sure that you will receive the data after paying the ransom. If you pay the ransom, it is only going to encourage the hackers to carry out more such attacks on you, as now they have identified you as someone who is willing to pay. In conclusion, one should never pay the ransom no matter what.
The Amount of Ransom Received By Hackers
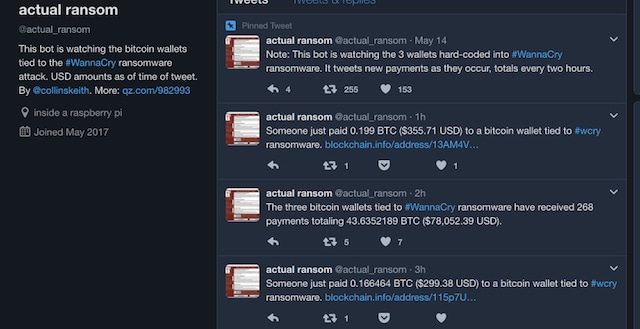
Even after knowing the negatives of paying the ransom, many people pay it, as they are too afraid of losing their data and hope that the extorters remain true to their word. A twitter bot has been created by Keith Collins, who is data/graphics developer at Quartz. The @actualransom Twitter bot keeps track of the ransom money.
As per the description, the bot is watching 3 wallets hard-coded into the WannaCry ransomware and tweets every time money is deposited into any of the wallets. At every two hours, it also gives the total amount deposited till now. At the time of writing, over $78,000 has been paid in ransom to hackers.
Protect Your PC From WannaCry Ransomware
Nothing can guarantee a full-scale protection against a ransomware until and unless you as a user became vigilant. There are some basic rules here. Stop downloading software from unverified sites and keep a keen eye on all your emails. Do not open links or download files contained in an email from an unverified user. Always check the sender’s email to confirm its source.
Apart from being vigilant, make sure to create a backup of all the important data in your computer if you have not already done so. In the off chances, your system is attacked, you can be sure that your data is safe. Also, install the latest Windows security updates. Microsoft has released a patch for the SMB exploit even for the non-supported version of Windows like XP, so immediately install the patch.
There are some other ways to protect your PC from a ransomware and you can check out our detailed article on the same.
SEE ALSO: 6 Best Anti-Ransomware Software To Protect Your Files
Stay Safe From WannaCry Ransomware
WannaCry has caused a huge havoc around the world and hence Windows users are naturally afraid. However, in most of the cases it’s not the platform but the user who is responsible for making such attacks successful. If users follow clean practices like installing and using latest version of the OS, installing security patches regularly and refraining from visiting malicious/shoddy websites, the risk of getting attacked by a ransomware like WannaCry is severely minimised.
I hope that the article has left you a little more informed about WannaCry ransomware. If you still have any doubts feel free to ask questions in the comment section below.


















