
Over the past few years, scores of data breaches of big companies like Facebook and Yahoo have made us wary of the tendency of online databases to be vulnerable. But most often, we imagine repercussions in the terminology of passwords and the data we enter online, with SMSes easily escaping the inventory of potential culprits.
A recent investigation by TechCrunch has led us to contemplate the ease with which SMSes can be exploited to hijack different accounts. The server of Voxox, a cloud communications company which offers SMS services enterprises – among other operations, could be accessed without a password. The database is now offline, but the damage could already have been done. Voxox says it’s currently evaluating the impact.
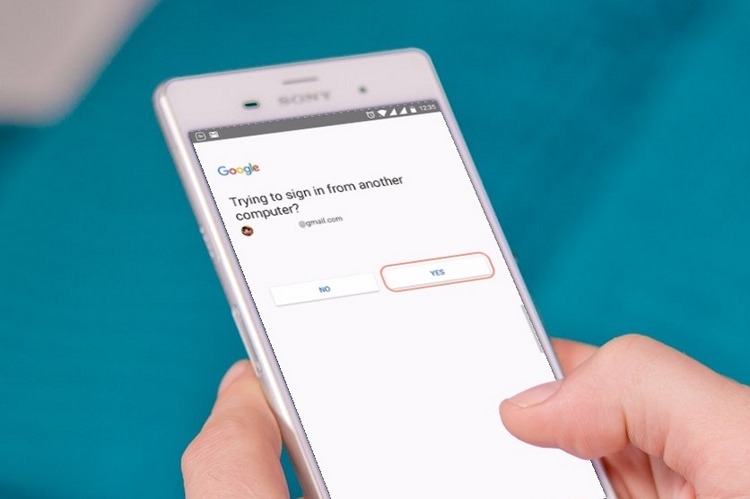
This lack of security gave hijackers an easy pass into the “a near-real-time stream of text messages“, it was reported. This vulnerability was discovered by a German bug bounty hunter, Sébastien Kaul. This database was available via Shodan, a public platform for databases intended for wider reach and not usually controlled by corporations.
Kaul easily got access to 26 million text messages, with neatly stacked metadata which made it easy to squeeze out information like names, real-time one-time passwords, internet banking codes, and even two-factor authentication keys.
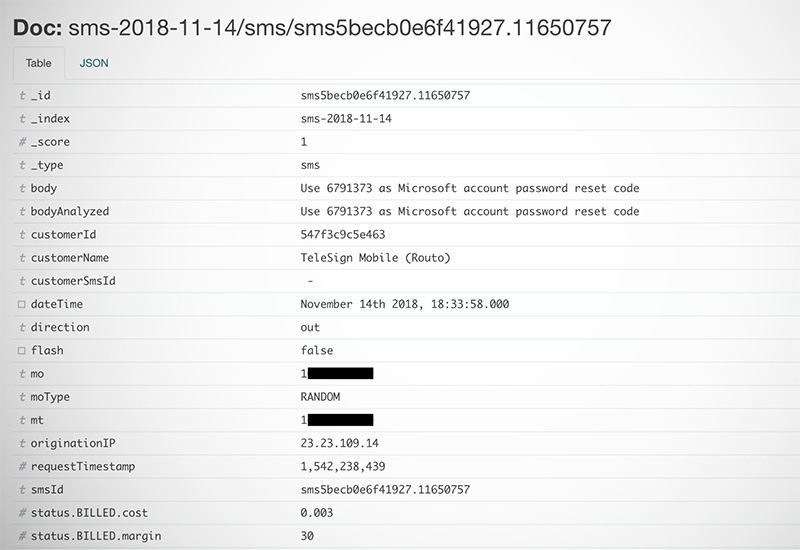
The sheer variety of data that is up for grabs publicly is an eye-opener. Here are the services that TechCrunch has noted could be exploited in case the database is breached:
- First-time verification codes for services such as Viber messenger, online quiz app HQ Trivia, some medical facilities
- 2FA codes and access codes for accessing accounts related to Google, Yahoo, Booking.com, Fidelity Investments
- Password reset links and codes for Microsoft and Huawei accounts
- Shipping notification from Amazon along with a link for tracking without any credentials
- And even, unencrypted and unprotected passwords for LA-based dating app Badoo
Another security researcher, Dylan Katz who reviewed these findings, also cautioned about “the potential that this has already been abused“. If it has, its reach could have a catastrophic impact on the users whose data was reportedly leaked.
Use Google Authenticator Not SMS for 2FA
While the impact of this leak is not currently measurable, we recommend you to use Google Authenticator app (free) which generates short–lives numeric codes for the purpose of 2-Factor Authentication. Although, it must be noted that Authentication runs on a device and the data is not stored on the cloud. While that ensures more security, you might be locked out if you lose your smartphone or have it stolen.










