
The recently discovered Meltdown and Spectre CPU vulnerabilities have sent the whole industry into a frenzy, and while they are currently being fixed through updates, the very solution is now proving to be another major headache.
First, it was the severe performance slowdown after installing the security patch, and now, there are reports of fake Meltdown and Spectre patch being spread for phishing attacks.
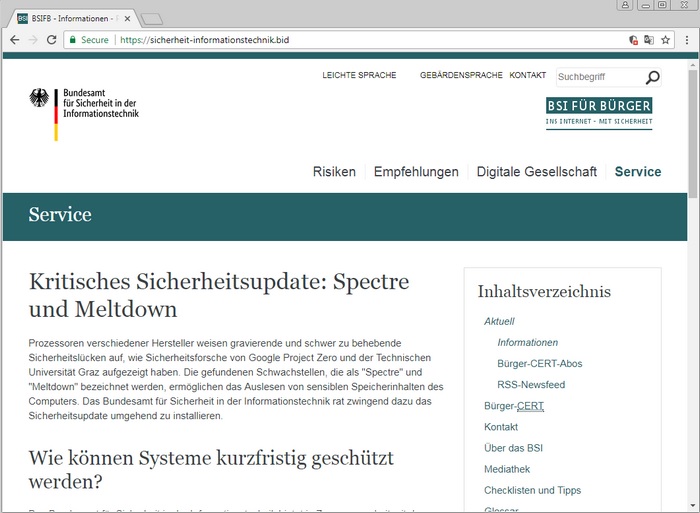
According to a report, an SSL-enabled domain imitating the official website of Germany’s Federal Office for Information Security (Bundesamt für Sicherheit in der Informationstechnik or BSI in short) is being used to do the dirty deed.
The fake website offers information about the Meltdown and Spectre vulnerabilities through various links that are supposed to direct users to resource banks where they can get an in-depth grasp of the whole fiasco.
The fraudulent website also hosts a ZIP archive link titled ‘Intel-AMD-SecurityPatch-11-01bsi.zip’, which supposedly contains the official patch for the aforementioned vulnerabilities. However, the ‘patch’ file is nothing but a cleverly disguised malware bank, which does one thing and one thing only i.e. install an information-stealing malware called Smoke Leader.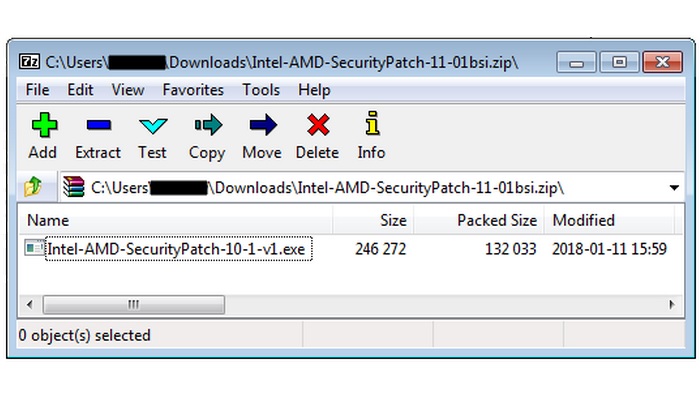 Security experts have discovered that once a system is infected with the malware, it connects to various domains and sends user’s private information stored on their PC to malicious parties in an encrypted form.
Security experts have discovered that once a system is infected with the malware, it connects to various domains and sends user’s private information stored on their PC to malicious parties in an encrypted form.
The German federal agency had earlier warned users about fake BSI emails being sent to users in the guise of officially distributed messages. In a press release, BSI clearly said:
“In the context of the recently announced “Specter” and “Meltdown” vulnerabilities, the BSI is currently monitoring a SPAM wave with alleged security warnings from the BSI. The recipients are prompted to perform security updates that can be retrieved using a link contained in the mail. The link leads to a fake website, which has similarity to the citizen website (www.bsi-fuer-buerger.de) of the BSI. The download of the alleged update leads to a malware infection of the computer or smartphone.”
The agency advised users to delete all such emails, and in case they have clicked on a link mentioned in the fake e-mail and opened a webpage, they should not download any content from the webpage.
As of now, the reports of such veiled attacks for spreading the Smoke Leader malware have been limited to Germany, but we advise users across the globe to refrain from downloading any patch which is not from an authorized source or appears sketchy.










