
After Spectre and Meltdown, Intel chips are on the news again for a new vulnerability. The newest threat is called Load Value Injection and it allows attackers to access Intel’s Software Guard eXstensions (SGX) – the part responsible for storing sensitive information.
“LVI is a new class of transient-execution attacks exploiting microarchitectural flaws in modern processors to inject attacker data into a victim program and steal sensitive data and keys from Intel SGX, a secure vault in Intel processors for your personal data.”, wrote the researchers on the website detailing the vulnerability.
The vulnerability was first discovered by the researchers from imec-DistriNet, KU Leuven, Worcester Polytechnic Institute, Graz University of Technology, the University of Michigan, the University of Adelaide, and Data61. It was then independently discovered by professionals at cybersecurity firm Bitdefender.
Just like Spectre, LVI exploits speculative execution. As detailed by the researchers, LVI is a hybrid of Spectre and Meltdown where the attackers gain the ability to alter or inject the data into the SGX system. Below is a flow diagram demonstrating the process.
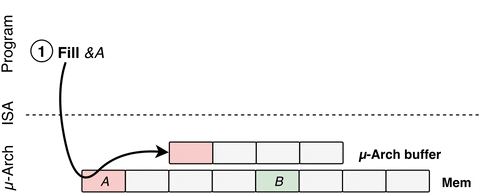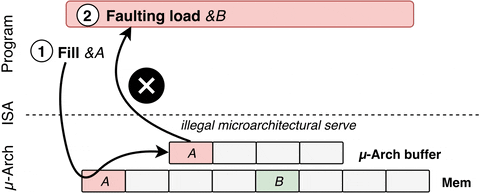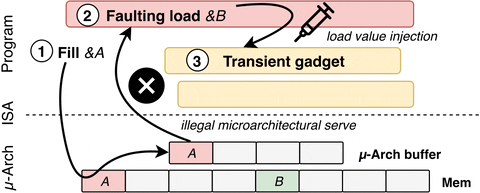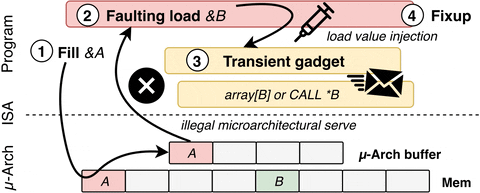
You probably need not worry about LVI as the attack is highly complex in itself and general users are not the ideal target for this attack. “Crucially, LVI is much harder to mitigate than previous attacks, as it can affect virtually any access to memory. Unlike all previous Meltdown-type attacks, LVI cannot be transparently mitigated in existing processors and necessitates expensive software patches, which may slow down Intel SGX enclave computations 2 up to 19 times.”
Intel is aware of the situation and has given the vulnerability a “medium” severity. In fact, the chipmaker has started rolling out an update for the SGX Platform Software (PSW) and SDK to mitigate the issue.
Here is what Intel has to say regarding LVI: “Due to the numerous complex requirements that must be satisfied to successfully carry out the LVI method, Intel does not believe LVI is a practical exploit in real world environments where the OS and VMM are trusted.”
You can learn more about LVI in the detailed research paper published on this website. Also, do not forget to watch the dramatic teaser video and demonstration video published by the researchers.