WhatsApp, a popular instant messaging platform now owned by Facebook with over 1.5 billion users across the globe has a major vulnerability that has not been fixed completely so far. The vulnerability was discovered by researchers at Check Point and was made public in Black Hat 2019, an annual Black Hat security conference.
The researchers claim to have found three methods of attack to intercept and gain access to Whatsapp messages. The first attack makes use of the quote feature to alter the identity of the message sender in a group. This can be done to indicate people who are not even a member of the group. Sounds crazy, right?
The second attack allowed attackers to entirely change the text in a person’s message. This indeed sounds serious and must get high priority from WhatsApp as it would essentially make people accountable for something they might have never said.
The third attack allowed the attackers to send a private message to the member of a group. While the message looks like a private conversation to the recipient, it will be shown to everyone in the group.
Of these three attacks, WhatsApp has fixed only the third vulnerability as of now. While Check Point had taken all efforts they could to make WhatsApp aware of the seriousness of these flaws, there has been no steps so far.
To prove their claims, the Check Point research team has created a tool that allowed them to provide proof-of-concept. If you’re curious, take a look at the below video to know how their tool works as shown by the team in a demonstration.
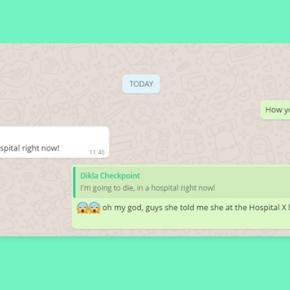
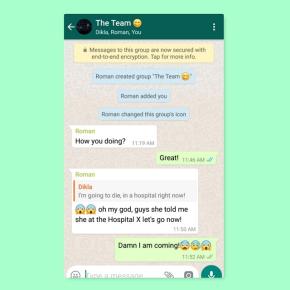
Below is a conversation the researchers made as part of testing. While these look funny at first glance, we must be aware of the impacts these kinds of vulnerabilities could cause in real life.
As you can see, the message originally sent was “Great!” which got modified into “I’m going to die in a hospital right now” which indeed depicts how serious of an issue this is.
We hope WhatsApp takes the necessary steps to fix these flaws as soon as possible. So, what do you think of this situation? Share your thoughts in the comments section below.