These days some tech companies seem more concerned about how to grow the user-base, than securing their servers or keeping user data private.
We’ve seen OnePlus and Xiaomi both operating unsecure payments gateways, but it has now been discovered that Truecaller Pay’s server was also openly accessible up until a while ago.
As reported by Redditor always_say_this, he had been tinkering around and come across a vulnerable server that was being used for Truecaller Pay transactions. Once you have access to this server, you could essentially see each and every transaction which was being completed using UPI-based Truecaller Pay.
All Your Data Is Accessible
The biggest concern, however, was not that you were able to see each transaction instead it was that the personal data – related to the transaction – was widely available for anyone to access. You could see the following via the loophole in the server:
- UPI Virtual Payment Address of the sender and receiver,
- Account numbers
- Account balance of the sender,
- Transaction status – success or failure,
- Device details – IMEI and IP address
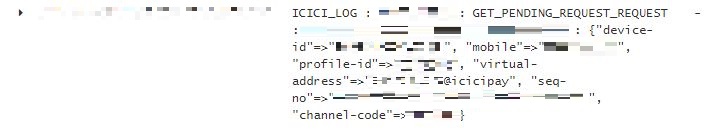
This is a grave miscarriage of security on the company’s part, who was instantly informed about the loophole by the Redditor yesterday evening.
Truecaller then released an official statement (on Twitter) saying that it was just a test server that was being “used for experimental provisioning of new services” and no data had been breached.
But, always_says_this wasn’t ready to give up and retorted that the server was still very much up and running. He included proof that it wasn’t a test server as one could clearly see ‘production’ highlighted in the screenshot he posted. So, we decided to get in touch with him to dig deeper into the security implications of this loophole.
Server Is Now Patched
While we were discussing the implications of this loophole, Truecaller confirmed that they have patched the vulnerability. The company said that the server is actually in production (means all services are running off it) but all the data one sees is not from real-world transactions.
They add that it’s a testing environment, which is the primary reason for the UPI ID in the screenshot attached above being @icicipay and not @icici. If the server was showing real-world transaction details, then the latter would’ve been used in the VPA. Truecaller further added,
@icici is the one used in current version of Truecaller, so this is why we say @icicipay is currently in a testing environment.The logs you access belong to a service in development which is yet to be hardened with the bank class security.
While we’d like to commend Truecaller for fixing this issue within 24 hours, the question is why would the company even test new services on an unsecured server. As the digital landscape of the country is growing quite exponentially, cybersecurity standards also need to catch up to keep our personal data secure. Fortunately, now there’s nothing to worry about in terms of Truecaller Pay and you may use it without any worries.










